How SASE Supports Continuous Threat Detection and Response
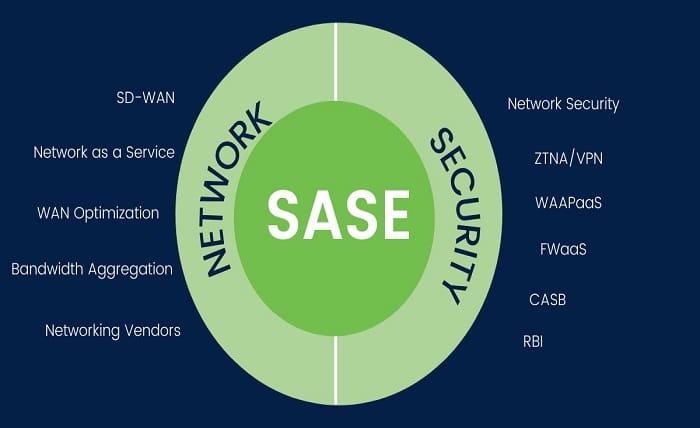
Safeguarding networks has become more critical than ever. Cyber threats are becoming increasingly sophisticated, and traditional methods of network security often fall short. This is where Secure Access Service Edge plays a transformative role. But what makes it such a game-changer? Let’s explore how such services support continuous threat detection and response.
Seamless Network and Security Integration
A key benefit of SASE is its ability to seamlessly integrate network and security functions. Integration is not just about connecting various elements; it’s about creating a cohesive system that allows for continuous detection and response.
Combining network and security into a single framework enables organisations to monitor their entire infrastructure from a unified perspective. This view is crucial for identifying and mitigating threats in real-time without the delays often caused by fragmented systems.
End-to-End Visibility
Visibility is paramount when it comes to detecting and responding to threats. Such services provide end-to-end visibility across the entire network, making it easier to detect anomalies and potential threats.
This comprehensive insight allows for quickly identifying unusual patterns that may indicate a security breach. With this level of visibility, security teams can respond to threats before they escalate. It also helps reduce the risk of a significant impact on the organisation.
Continuous Monitoring and Real-Time Response
The quicker a threat is detected, the faster it can be neutralised. Such services excel in providing continuous monitoring capabilities, ensuring that threats are detected in real time. It is a crucial advantage over traditional security models, which rely on periodic scans or manual checks.
With such services, the network is constantly under surveillance, allowing for immediate response to any detected threats. This continuous monitoring is a key component of an effective threat detection and response strategy, as it minimises the window of opportunity for attackers.
Proactive Threat Mitigation
One of the standout benefits is its ability to mitigate threats proactively. Instead of merely reacting to incidents after they occur, such services can identify potential risks before they fully develop. By analysing network traffic and user behaviour patterns, they can detect early signs of malicious activity and take preemptive action.
Enhanced Security Through Service Chaining
Service chaining allows for integrating multiple security functions, such as firewalling, intrusion detection, and secure web gateways, into a single, streamlined process. This approach enhances threat detection and response by ensuring that all security measures work together efficiently. The result is a more robust defence mechanism that can adapt to evolving risks, providing continuous protection across the network.
Scalability and Flexibility
Such services are designed to be scalable and flexible, which is essential in today’s business environments. They can easily scale to accommodate these changes, ensuring continuous protection without a complete overhaul of the security infrastructure. This scalability also means that SASE can adapt to different network architectures, whether it’s a small business or a large enterprise.
Improved User Experience
A critical aspect of any security solution is its impact on the user experience. Traditional security models often slow down network performance or create bottlenecks, which leads to frustration among users.
On the other hand, such services are designed to provide robust security without compromising performance. By optimising data flow and ensuring that security measures are integrated seamlessly, the overall user experience is enhanced. This balance between security and performance is crucial for maintaining productivity while ensuring continuous protection.
SASE offers many benefits, making it an essential tool for continuous threat detection and response. It redefines how organisations approach network security from seamless integration to proactive threat mitigation. By adopting it, businesses can ensure that their networks are protected around the clock, giving them the peace of mind to focus on what matters most—growing their business.